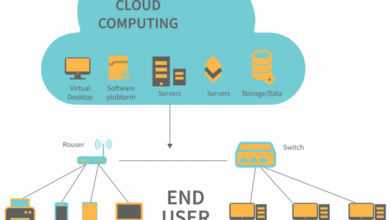
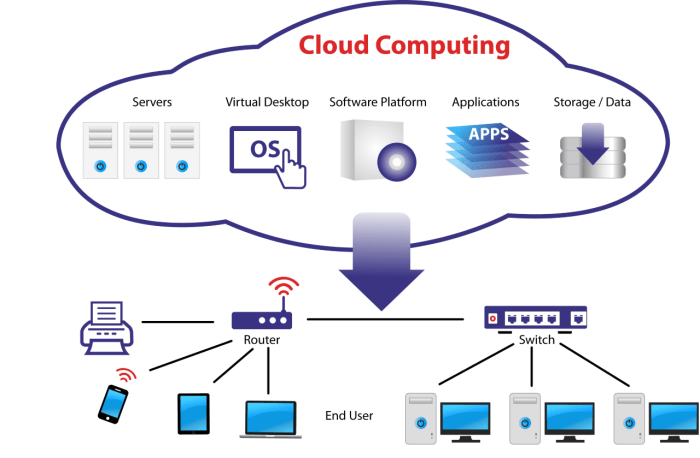
Empowering Security: How Cloud Architecture Diagrams Fortify Your Digital Defense
In the ever-evolving landscape of cybersecurity, cloud architecture diagrams have emerged as a game-changer, providing organizations with an invaluable tool to bolster their security posture. These visual representations of cloud infrastructure offer a comprehensive roadmap, enabling security teams to navigate the complexities of cloud environments and proactively address potential vulnerabilities.
By harnessing the power of cloud architecture diagrams, organizations can gain unprecedented visibility into their cloud infrastructure, streamline security audits, foster effective collaboration, and continuously optimize their security posture. Join us as we delve into the transformative impact of cloud architecture diagrams on security, exploring how they empower organizations to fortify their digital defenses and stay ahead of evolving threats.
Enhanced Visibility and Control
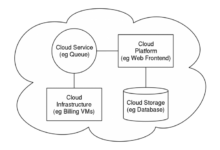
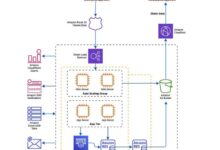
Cloud architecture diagrams are pivotal in enhancing visibility and control over security aspects. These diagrams provide a comprehensive visual representation of the cloud environment, enabling security teams to:
Improved Identification of Vulnerabilities
- Gain a holistic view of the cloud infrastructure, including its components, interconnections, and data flows.
- Identify potential vulnerabilities and security gaps by analyzing the relationships between different cloud components and services.
- Proactively address security risks by implementing appropriate countermeasures and hardening configurations.
Centralized Monitoring and Management
- Enable centralized monitoring and management of security controls across the entire cloud environment.
- Streamline security operations by providing a single pane of glass view of security events, alerts, and logs.
- Facilitate proactive threat detection and response by enabling security teams to quickly identify and mitigate security incidents.
Improved Communication and Collaboration
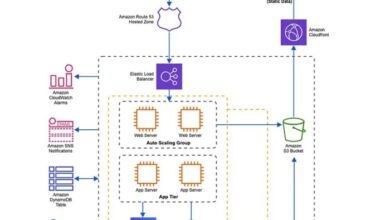
Cloud architecture diagrams serve as effective tools for facilitating seamless communication and collaboration among security teams. These visual representations provide a common ground for security professionals to discuss and align their strategies, ensuring that security measures are in sync with the overall business objectives.
Shared Understanding of Security Risks and Responsibilities
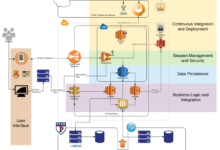
Cloud architecture diagrams play a crucial role in fostering a shared understanding of security risks and responsibilities within an organization. By visualizing the interconnected components of the cloud infrastructure, security teams can gain a comprehensive view of potential vulnerabilities and attack vectors.
This shared understanding enables teams to collaborate more effectively in developing and implementing security measures, ensuring that all aspects of the cloud environment are adequately protected.
Streamlined Security Audits and Compliance
Cloud architecture diagrams simplify security audits and compliance assessments by providing a comprehensive visual representation of the cloud infrastructure, its components, and their interconnections. This visual representation enables auditors to quickly grasp the overall security posture of the cloud environment, identify potential vulnerabilities, and assess compliance with regulatory standards.
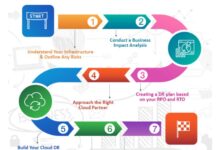
Step-by-Step Guide to Demonstrating Compliance
To use cloud architecture diagrams to demonstrate compliance with regulatory standards, follow these steps:
- Identify Applicable Regulatory Standards: Determine the relevant regulatory standards that apply to your organization and cloud environment. Examples include ISO 27001, HIPAA, PCI DSS, and GDPR.
- Map Cloud Architecture to Regulatory Requirements: Map the components and interconnections of your cloud architecture to the specific requirements of the regulatory standards. This mapping helps identify gaps and areas where additional security measures are needed.
- Create a Compliance Matrix: Develop a compliance matrix that links the cloud architecture components to the regulatory requirements. This matrix serves as a comprehensive reference for auditors to assess compliance.
- Conduct Regular Audits: Regularly review and update the cloud architecture diagrams and compliance matrix to ensure ongoing compliance. This includes incorporating changes to the cloud infrastructure, security controls, and regulatory standards.
Best Practices for Maintaining and Updating Diagrams
To ensure ongoing compliance, maintain and update cloud architecture diagrams by following these best practices:
- Centralized Repository: Store cloud architecture diagrams in a centralized repository that is accessible to all relevant stakeholders, including auditors and compliance teams.
- Regular Reviews: Conduct regular reviews of the cloud architecture diagrams to identify any changes or updates that need to be made.
- Version Control: Implement version control for cloud architecture diagrams to track changes over time and easily revert to previous versions if necessary.
- Collaboration and Communication: Encourage collaboration and communication among the IT, security, and compliance teams to ensure that the cloud architecture diagrams accurately reflect the current state of the cloud environment.
Risk Assessment and Mitigation
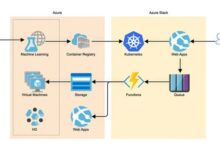
Cloud architecture diagrams are instrumental in identifying and assessing security risks by providing a comprehensive visual representation of the cloud environment. This holistic view enables security teams to pinpoint potential vulnerabilities, such as exposed ports, unencrypted data, and weak access controls, which may otherwise remain hidden.
Prioritizing Security Vulnerabilities
By mapping out the relationships between cloud components, cloud architecture diagrams facilitate the prioritization of security vulnerabilities based on their potential impact on business operations and data integrity. This prioritization process considers factors such as the sensitivity of the data, the likelihood of an attack, and the potential consequences of a successful breach.
Developing Risk Mitigation Strategies
Cloud architecture diagrams serve as a foundation for developing and implementing effective risk mitigation strategies. By understanding the interdependencies between cloud components and the flow of data, security teams can identify appropriate countermeasures to address specific vulnerabilities. These measures may include implementing encryption, enforcing access controls, and deploying security monitoring tools.
Continuous Improvement and Optimization
Cloud architecture diagrams are essential tools for driving continuous improvement and optimization of an organization’s security posture. By providing a comprehensive and visual representation of the cloud environment, these diagrams help security teams identify vulnerabilities, gaps, and areas for improvement.
Regularly reviewing and updating cloud architecture diagrams enables organizations to:
Identify Opportunities for Enhancing Security Controls and Measures
- Visualize Security Gaps: Diagrams help identify areas where security controls are lacking or inadequate, allowing teams to prioritize and address these gaps.
- Evaluate Control Effectiveness: By mapping security controls to specific cloud components, teams can assess their effectiveness and make adjustments to improve protection.
- Stay Current with Security Best Practices: Diagrams facilitate the incorporation of emerging security best practices and industry standards into the cloud environment.
Facilitate Regular Security Reviews and Updates
- Centralized Documentation: Diagrams serve as a central repository for security-related information, enabling teams to easily track changes, updates, and improvements.
- Collaboration and Communication: Diagrams foster collaboration among security teams, architects, and stakeholders, ensuring a shared understanding of the security posture and facilitating effective communication.
- Audit Preparation and Compliance: Diagrams simplify audit preparation and compliance efforts by providing a comprehensive overview of the cloud architecture and its security controls.
Case Studies and Real-World Examples
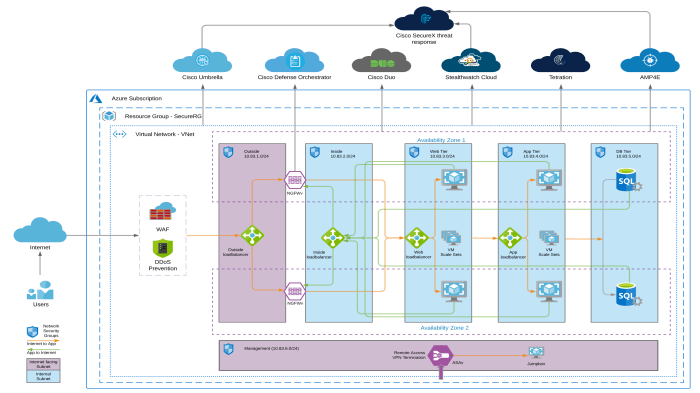
Organizations worldwide are leveraging cloud architecture diagrams to enhance their security posture. These diagrams provide a visual representation of the cloud environment, enabling organizations to identify vulnerabilities, enforce security policies, and respond to threats proactively.
Here are some notable case studies and real-world examples:
Financial Services Company:
- Challenge: The company faced challenges in maintaining compliance with regulatory requirements due to the complexity of its cloud infrastructure.
- Solution: The company implemented cloud architecture diagrams to visualize the infrastructure and identify potential compliance gaps.
- Benefits: The diagrams helped the company streamline its security audits and ensure continuous compliance with industry regulations.
Healthcare Provider:
- Challenge: The provider struggled to manage security risks associated with the integration of multiple cloud services.
- Solution: The provider used cloud architecture diagrams to map the interconnections between cloud services and identify potential attack vectors.
- Benefits: The diagrams enabled the provider to implement targeted security controls and mitigate risks effectively.
Retail Company:
- Challenge: The company faced difficulties in detecting and responding to security incidents due to the lack of visibility into its cloud environment.
- Solution: The company employed cloud architecture diagrams to gain a comprehensive view of its cloud infrastructure and improve incident response.
- Benefits: The diagrams helped the company reduce the time to detect and respond to security incidents significantly.
These case studies demonstrate the practical benefits of using cloud architecture diagrams to improve security. By visualizing the cloud environment, organizations can identify vulnerabilities, enforce security policies, and respond to threats more effectively.
Final Thoughts
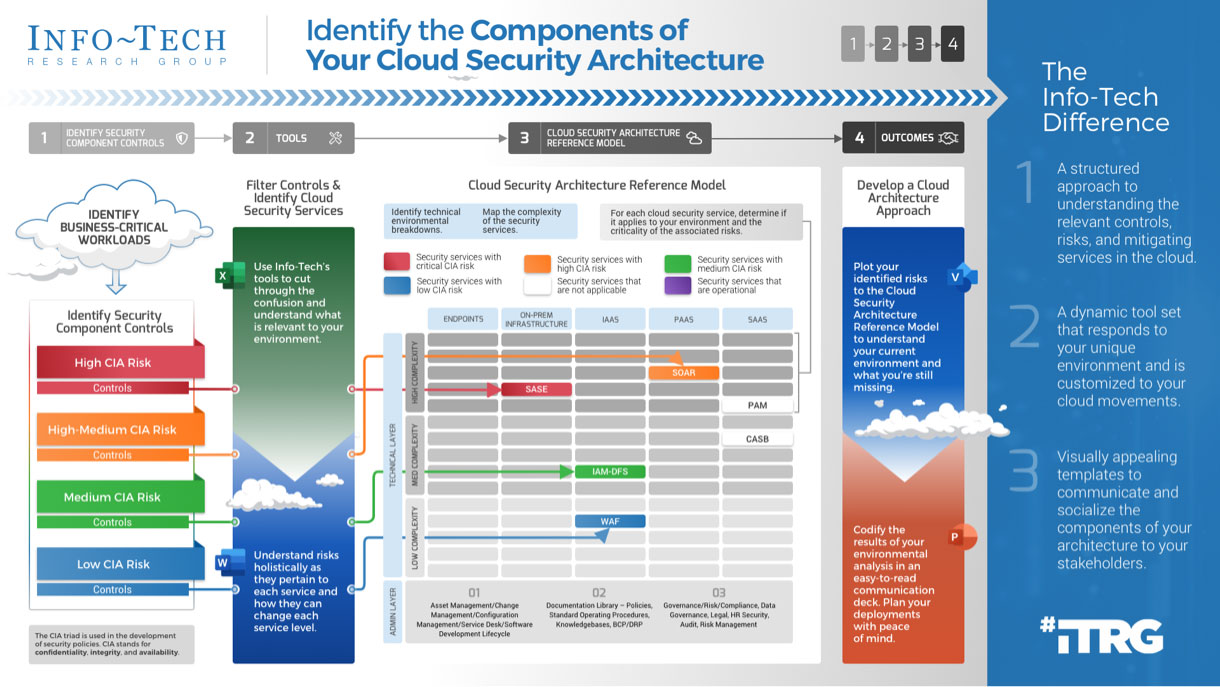
In conclusion, cloud architecture diagrams have revolutionized the way organizations approach security in the cloud. By providing a comprehensive visual representation of cloud infrastructure, these diagrams empower security teams with enhanced visibility, streamlined audits, effective collaboration, and continuous improvement. Embracing cloud architecture diagrams is a strategic move that enables organizations to proactively address security risks, optimize their security posture, and confidently navigate the ever-changing cybersecurity landscape.